A brief overview of the job done
And finally, Yes! We did it, it was not a complicated job but it was instead a bunch of different things, just as a memory refresh, these are the steps we had to follow in order to reach this point:
- Create a new session which uses password authentication method
- Generate SSH Keys and save them to computer
- Copy Public SSH Key to the remote server
- Map Private SSH Key to the session changing the authentication method
Log into your remote server using SSH Keys
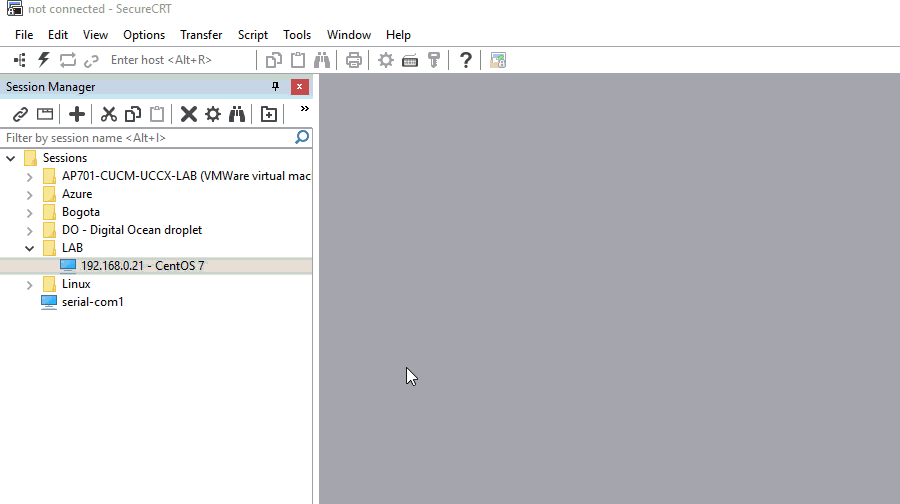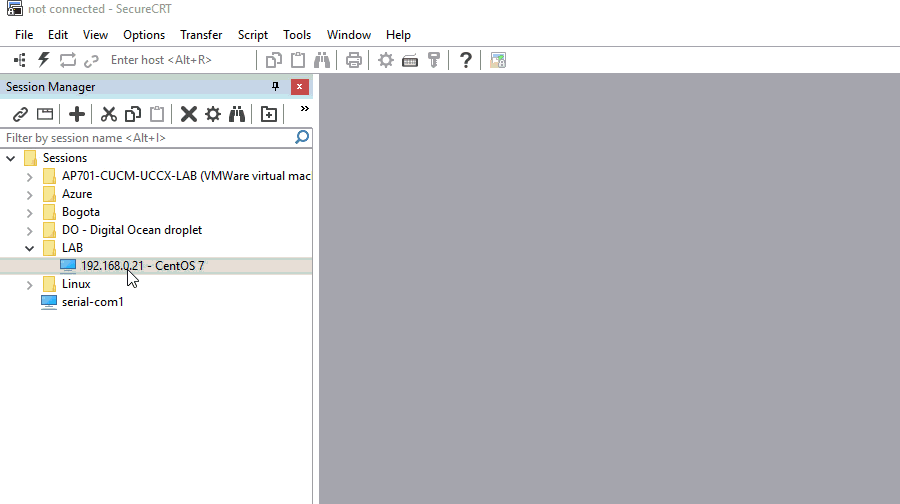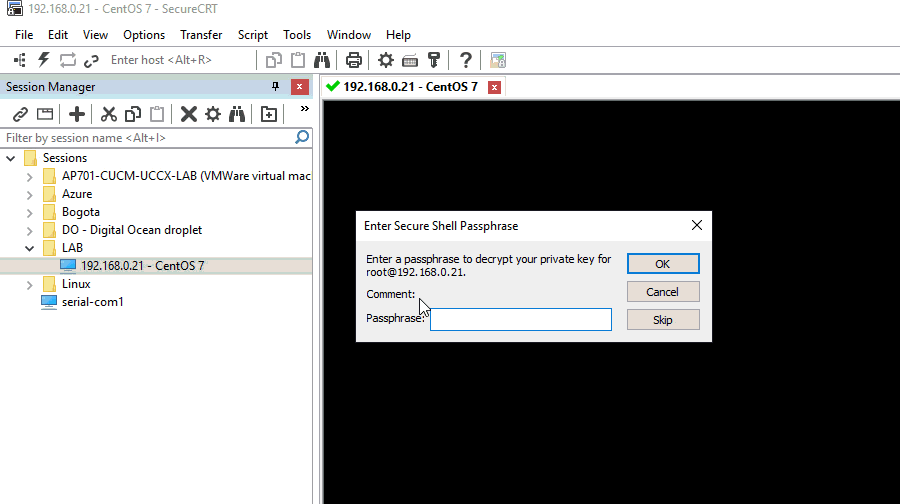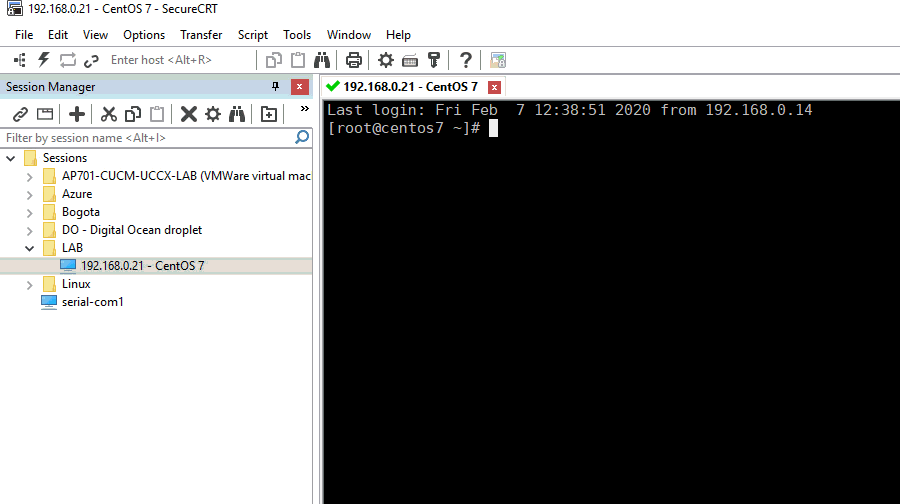
Protecting Private Key with a Passphrase
As best practices dictate our Private SSH key is properly protected by a “passphrase” this way if a malicious actor manage to get a copy of the key, He/She won’t be able to use it.
