The history of SSH
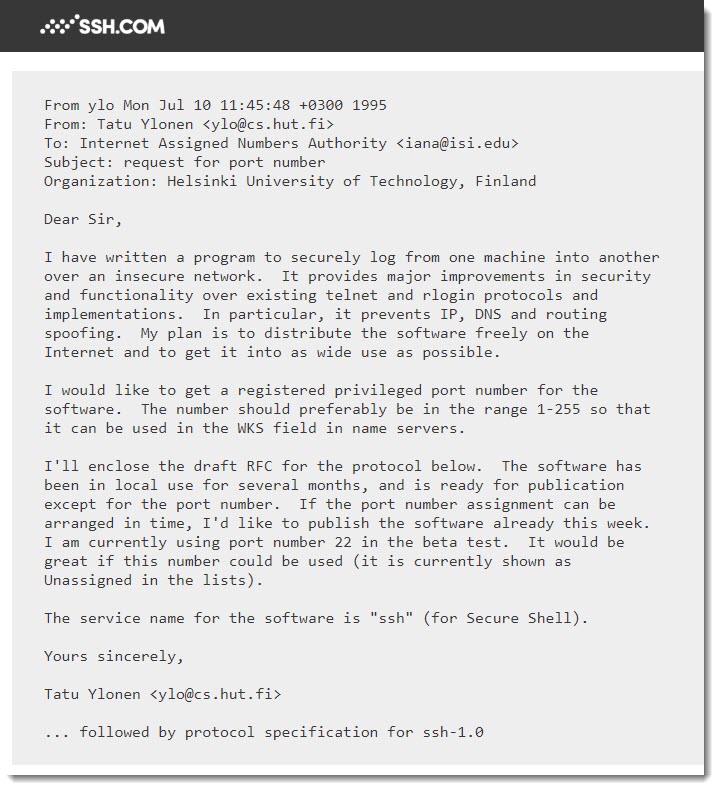
The initial version of SSH (Secure Shell) was written in 1995 when telnet and FTP were widely used, you can learn a little bit more about how Tatu Ylonen a Finland student from de University of Helsinki wrote the first version of SSH and why the TCP port number 22 was chosen in this website.
The main idea behind SSH was to allow secure connection from one computer into the other allowing people to work remotely.
Working from home is nowadays something quite common between computers/system administrators, you don’t want to spend much time working inside an ice cold Data Center, remote work is here to stay.
Open SSH
The first vesion of SSH evolved into Open SSH and now comes with every Unix, Linux, and Mac computer, but is also available for every other platform like MS Windows. It has become the de-facto tool for system and network administration over computer networks.
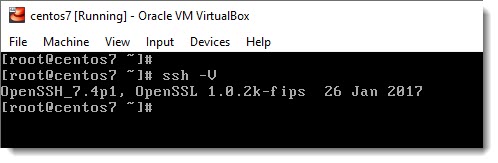
Checking Open SSH version on CentOS 7
Even though we’re working on LAB enviroment it is always a good idea to follow the security standards to be ready for the day when you move to the real life, I mean the moment when we move from the LAB to a VPS (Virtual Private Server).
ssh -V
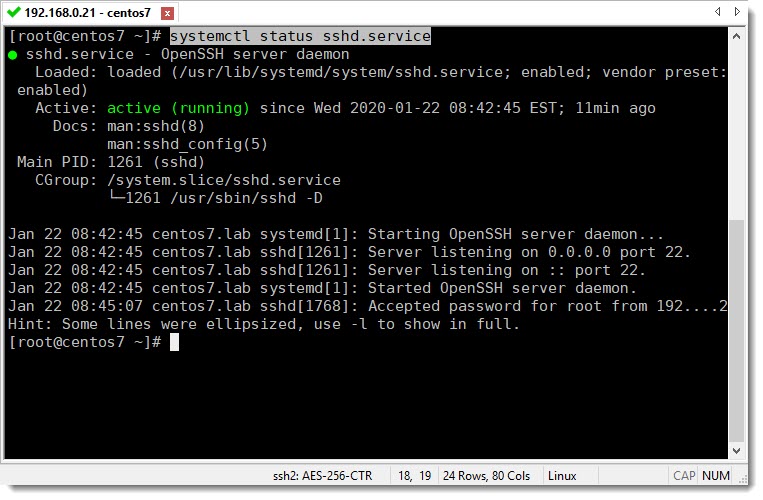
Checking Open SSH current status
If for some reason you are not able to connect to your CentOS via SSH, the first troubleshooting step is to be sure there is connectivity between your devices, for that you can use “ping“, and on the other hand, the second troubleshooting step will be to make sure that SSH is actually running, for that you can use the following CLI command:
systemctl status sshd.service
Linux CentOS SSH files and folders
The image below shows a typical Linux directory tree and also where are located the important SSH files, one of them is used to configure SSH globally (sshd_config) and the others belongs to each user and each user uses this file to keep their SSH Public Keys (authorized_keys).
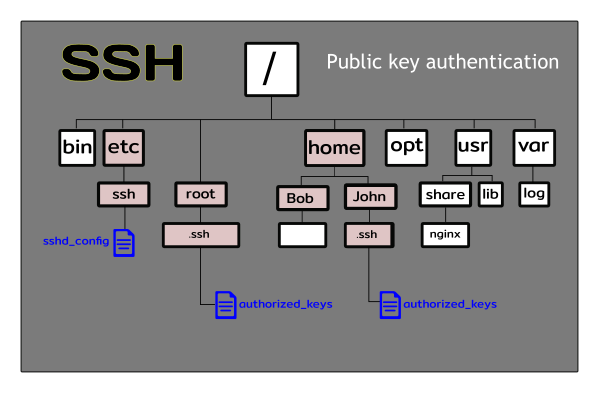
As you can see in the image above the user “root” is not inside the famous “home” folder as the rest of the users of the system, I know this could be at the beginning a little bit confusing, the purpose really is to secure this account as much as possible, and make sure you don’t treat the “root” user as any other user.
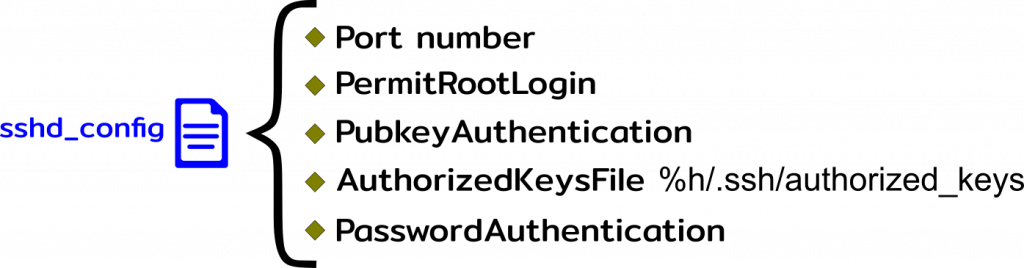
SSH Global Settings file
All the settings related to SSH are located inside the file called “sshd_config” and because of that this is one of the most important SSH files, and the first place you want to go to learn how your SSH is currently configured and to tweak it to fit your own preferences, the image below shows the most important parameters you will find inside this vital SSH file.
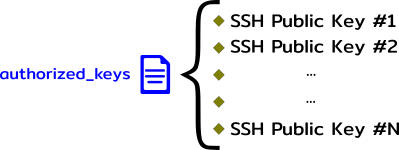
Authorized Keys file
In order to enable the authentication via SSH Public/Private keys, each user must have inside of its “home directory” a folder called “.ssh” and inside that folder a file called “authorized_keys“, all the public keys that are authorized to login into the machine must be there, you can simply copy and paste them immediately after they are created.
Where to go next?
Now that you know a little bit more about Open SSH we can move to the next step, we can generate a pair of SSH keys and you’ll see that it is a really quick process.