What are SSH keys?
SSH Keys are a pair of encryption keys that are mathematically linked to each other, in a way that one of them (public_key) could be generated from the other (private_key), but never the other way around, we usually refer to this as a one way process.
Where are SSH keys used?
SSH keys are used for authentication purposes for both users and servers, SSH keys provide a much robust protection than password authentication, which can suffer from “man-in-the-middle” attacks, and that’s why password authentication is only recommended to be used on LAB environments, for real world cases SSH keys authentication has become the industry standard.
Asymmetric Encryption
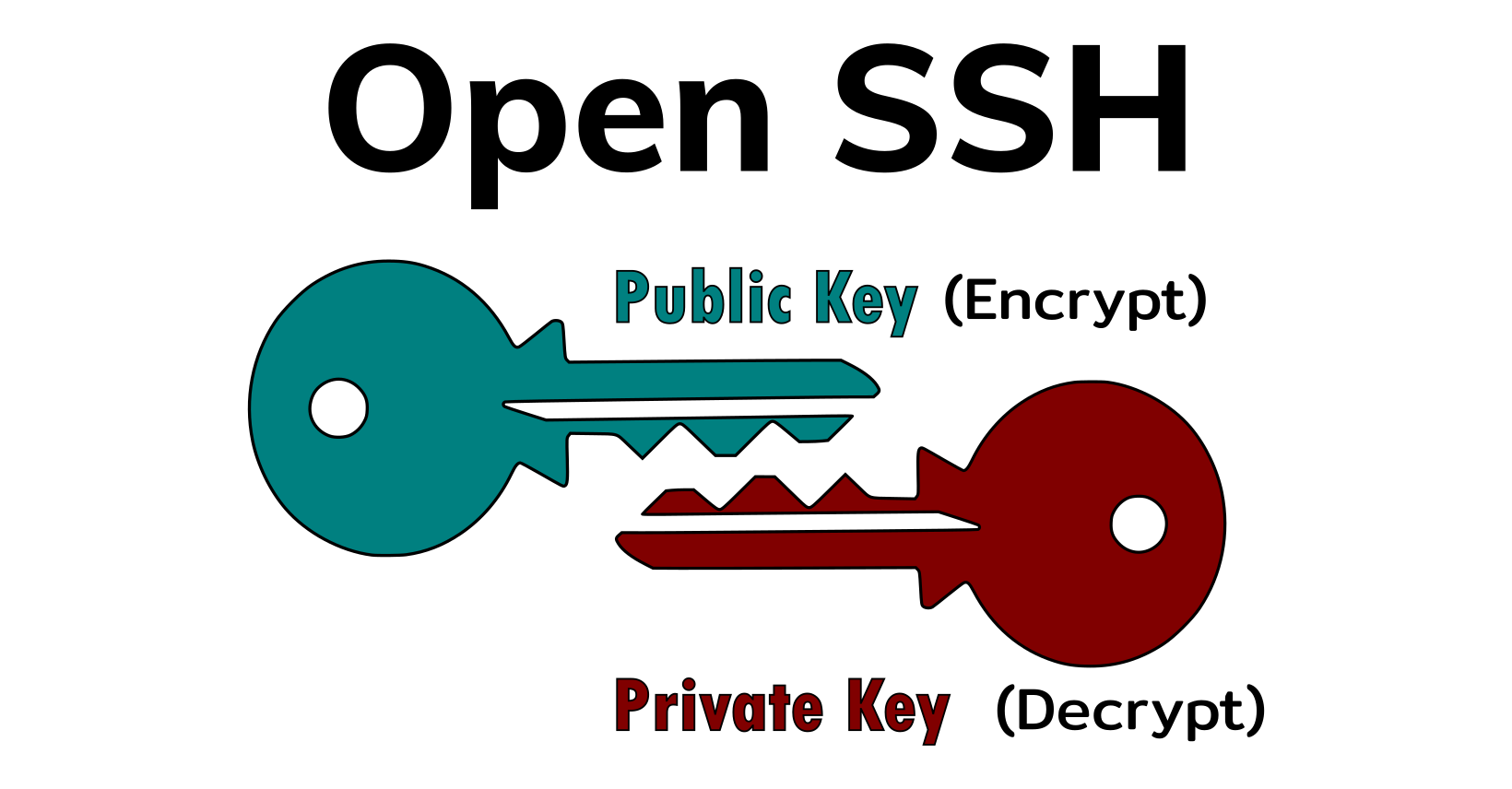
Have you ever heard about Asymmetric Encryption? The word “asymmetric” tell us that one key is used to encrypt (public key) and the other to decrypt (private_key), using the same logic it is easy to understand that on a “symmetric encryption”, the same key is used for both, encrypt and decrypt.
Public key authentication
Public key authentication/encryption are just others names to refer to the same subject, given that one of the keys is called “private key” and the other one is called “public key”, and as their names suggest one of them is meant to be kept private, like a top secret never to be revealed and the other one is kind of the opposite, it is meant to be shared with every person who wants to communicate with us, hence their name “public”.
How to protect the Private Key
Now that you know the importance of the “private key” you may wonder how to protect it, well, first of all is not recommended to move the private key from the computer where it was generated for obvious reasons, another good practice is not to use the same pair of keys to authenticate on all your devices it is always best to generate a new pair for every new device, and last but not least always use a “passphrase” to protect the key in the event that somebody manages to get a copy of the key from your computer, it will be useless without the passphrase.
Public Key exchange
Public keys are automatically exchanged while establishing the connection, during the process known as handshake.
Known keys are stored (saved locally) so that the verification dialog is not required on subsequent connections.
How SSH key are generated?
The SSH keys generation process involves mainly computational power because it applies an encryption algorithm to a big random number.
About Encryption Algorithms
There are multiple algorithms to generate public/private key pairs, the two most used nowadays are RSA and DSA, you can take a look at wikipedia.org to learn about them.
Importance of the randomness
Some applications make use an specific module refered to as the “random number generator” which do everything automatically, that is arguably good enough.
Other applications like puttygen (the ssh key generator tool for windows) actually lets the user move the mouse cursor randomly within the window to seed the random number generator, this is better than any pure program based generator would do.
Terminal/CLI based key generators can let the user type random keys on the keyboard in order to seed the random number generator.
Keys are very large integers with particular mathematical properties, computers cannot generate random numbers. The best they can do is measure natural phenomenon and apply the resulting data to complicated formula, producing close to random numbers. So we play on the keys for a while until the key generation software has gathered enough data.
How to generate SSH Keys
For an application to support SSH it is mandatory to be able of generate the pair of SSH keys Private/Public, in this article we’re going to cover the steps you must follow on SecureCRT, Putty and also WinSCP because these are the tools we are using on our LAB.